Simple LDAP
WARNING: This plugin should only be enabled and configured by system administrators as it affects how users log in to ResourceSpace.
This plugin allows users to log on to ResourceSpace using the same credentials that they use to log on to computers on your organisations network. It has been tested with Microsoft Active Directory and Oracle Directory servers.
Important information
- Please note that this plugin enables consistent sign-on (CSO) and not single sign-on (SSO). This means that users will still be required to enter a username and password in order to access the system. If you already have an organisation wide single sign-on system please refer to the simplesaml plugin.
- Whilst it is possible to use this on an externally hosted system, it is primarily intended for use on internal networks where the ResourceSpace server can communicate with the directory without requiring the directory server to be exposed to the Internet. If your ResourceSpace system is hosted externally we recommend discussing CSO and SSO with your internal IT group. Please ensure that if the LDAP plugin is used on a hosted site it is configured with secure LDAP (LDAPS).
Requirements
PHP ldap extension must be installed and enabled for the plugin to work.
Configuration
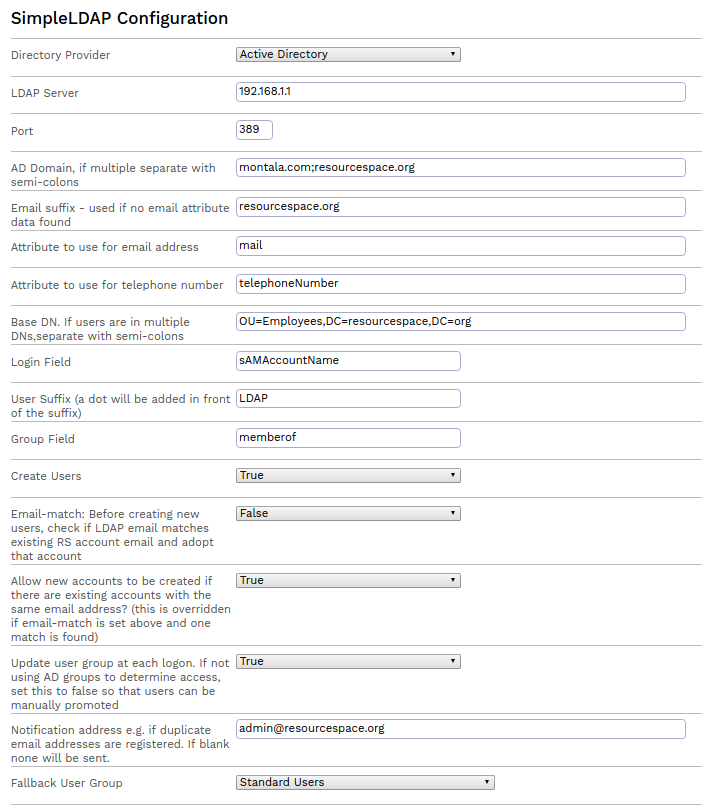
The plugin options page requires the following information to be provided:-
| Directory Provider |
Select the appropriate directory server. If using Open Directory, select the Oracle Directory provider. |
| LDAP Server | The IP Address or hostname of the directory server |
| Port | The TCP port of the LDAP server (usually 389, or 636 for LDAPS) |
| AD Domain | The domain name (e.g. resourcespace.com). If multiple domains, separate with semi-colons |
| Email suffix | This will be used to create the email address from the username if no email field is mapped |
| Attribute to use for email address | The LDAP attribute to retrieve the email address from |
| Attribute to use for telephone number | If relevant, the LDAP attribute to retrieve the phone number |
| Base DN | The branch of the directory that contains the users. This can be a high level of the tree or a list of OUs . If users are in multiple OUs they must be separated by semi-colons |
| Login Field | This is the directory attribute that matches the username (usually uid or sAMAccountName) |
| User Suffix | This will be added to the RS account so that the LDAP users can be distinguished from the standard ResourceSpace users. Can only be blank if no overlap between usernames is expected. A dot will be automatically be added in front of the suffix |
| Group Field | Field that contains the group memberships (or departments) of the user. Used to facilitate mapping of LDAP role groups to ResourceSpace user groups |
| Create Users | Create the users if they do not exist in RS already |
| Email-match | Before creating new users, check if email retrieved via LDAP matches an existing RS account email, and if so to 'adopt' that account. Useful if enabling LDAP on an existing system since it means users will retain collections and permissions |
| Allow new accounts to be created if there are existing accounts with the same email address? | This setting is overridden if 'email-match' is enabled as above and only one matching account is found |
| Update user group at each logon | If not using LDAP group memberships to determine access set this to false so that users can be manually assigned to appropriate user groups |
| Notification address | Email address to send simpleldap plugin notifications to e.g. if new LDAP users have the same address as multiple ResourceSpace accounts. If left blank no emails will be sent |
| Fallback User Group | New LDAP users will be added to this group if no match is found with a configured group mapping |
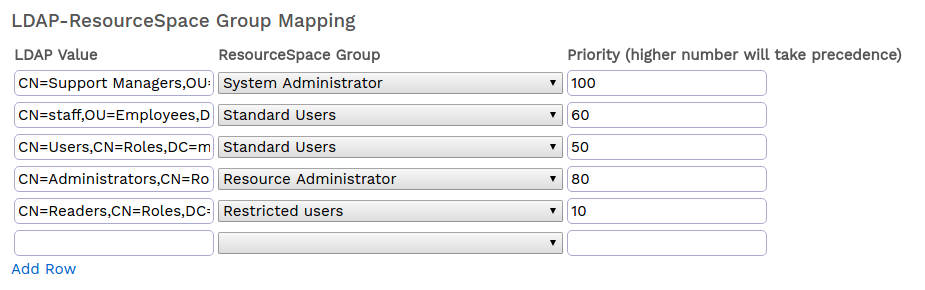
| LDAP-ResourceSpace Group Mapping | This list will be auto populated with discovered LDAP groups once users start to log on. Each group can be mapped to a RS group and assigned a priority. If the groups (usually full DNs) are known these can be input in advance. Each group mapping can be assigned a priority to deal with the usual situation that a user is a member of multiple LDAP groups. For example if it is required that membership of a media team group LDAP group take precedence over the general staff group mapping, the media team mapping should be assigned a higher number |
Testing
To test the LDAP configuration, click on the 'Test LDAP configuration' button
If the LDAP server cannot be contacted you will see the test fail. If you successsfully connect you can enter user credentials and click 'Test authentication'. This allows you to check that the authentication will work and that the group information is returned correctly.
Troubleshooting
If you experience issues with the LDAP plugin you can find additional useful information by enabling the ResourceSpace debug log and searching the log for entries that start with 'LDAP'.
Example configuration